Filling the cybersecurity gaps
This is evidenced by our 19-year history of ZERO plain Data breaches with organisations of all size and our unique ability to protect ALL types of Data, whether in-transit, in-use, or at-rest.

What makes the SecureAge Security Suite different?
The extended Suite combines protection for Data and Email with
- SecureDiskto flexibly encrypt full-disks for authorised users
- Create and mount virtual disks on all Windows platforms
- Simply drag and drop to encrypt and decrypt shared files
- Authenticate and control with digital signing for added security
- Flexibly manage multiple volumes at preferred sizes
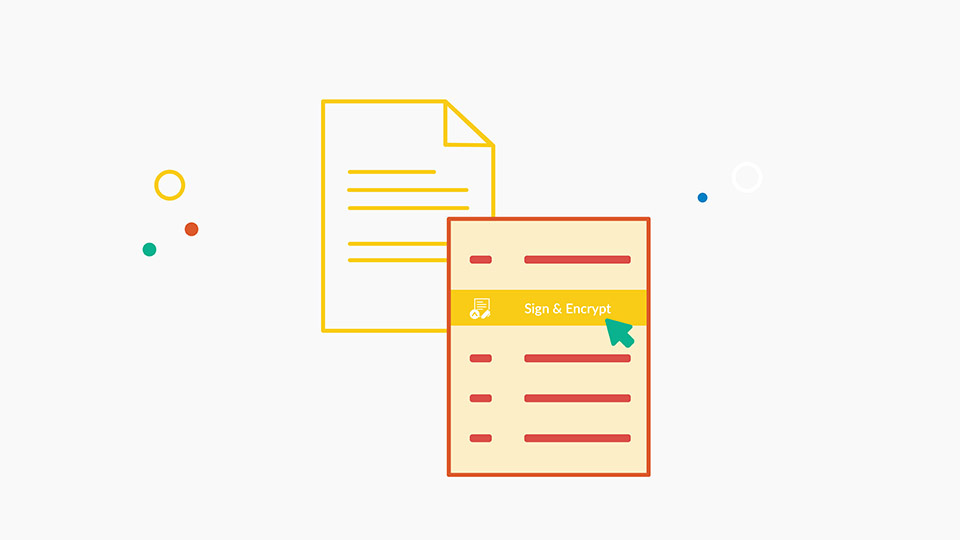
- DRM and digital signingto verify Data integrity and authenticity of sender
- Securely sign documents so recipients can be assured they are from the original sender
- Permanently delete documents without leaving a trace
- Built-in key and signature management
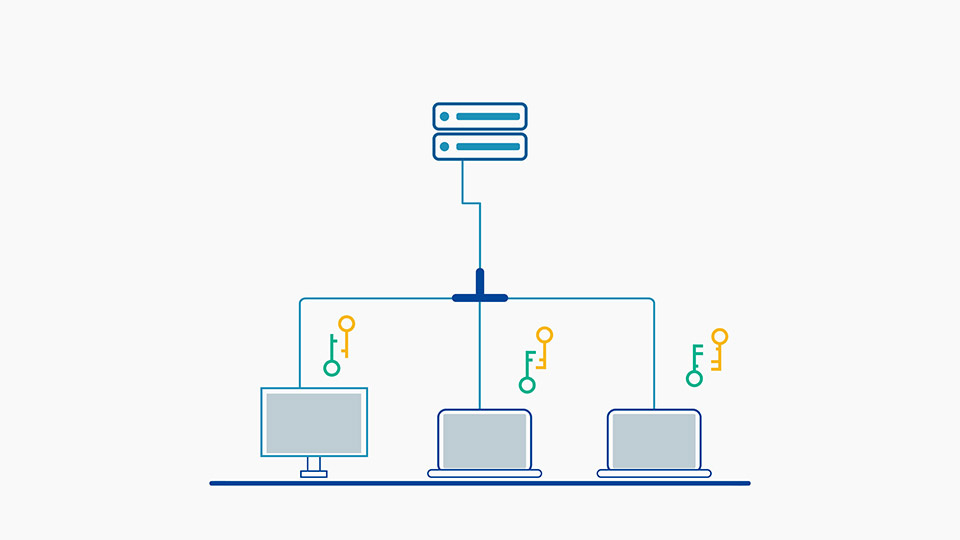
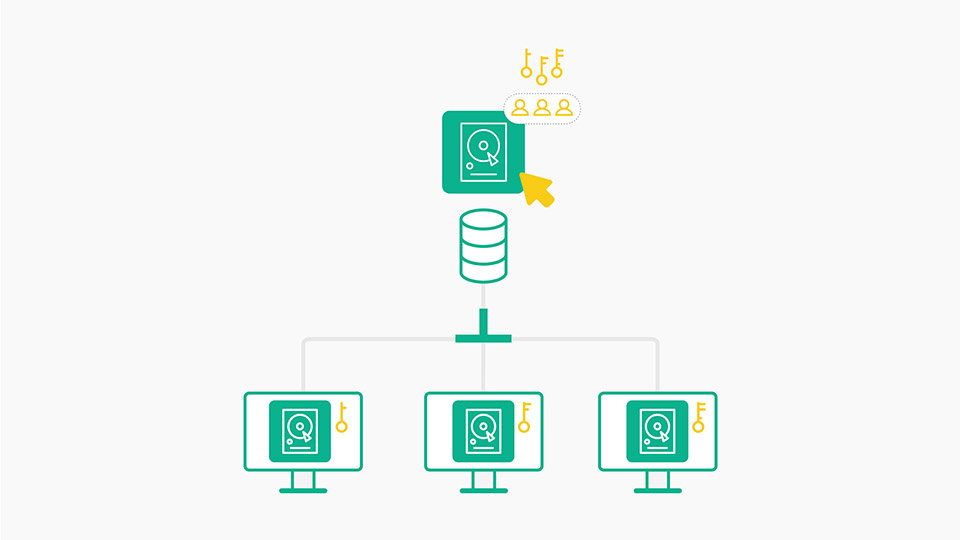
This is a comprehensive PKI-based feature that secures ALL files with 256-bit AES (Advanced Encryption Standard) file encryption, digital signing and digital rights management (DRM). ALL files are protected from unwanted tampering and interception ensuring privacy, integrity, and authenticity.
- Application controlto ensure only trusted applications are allowed to run
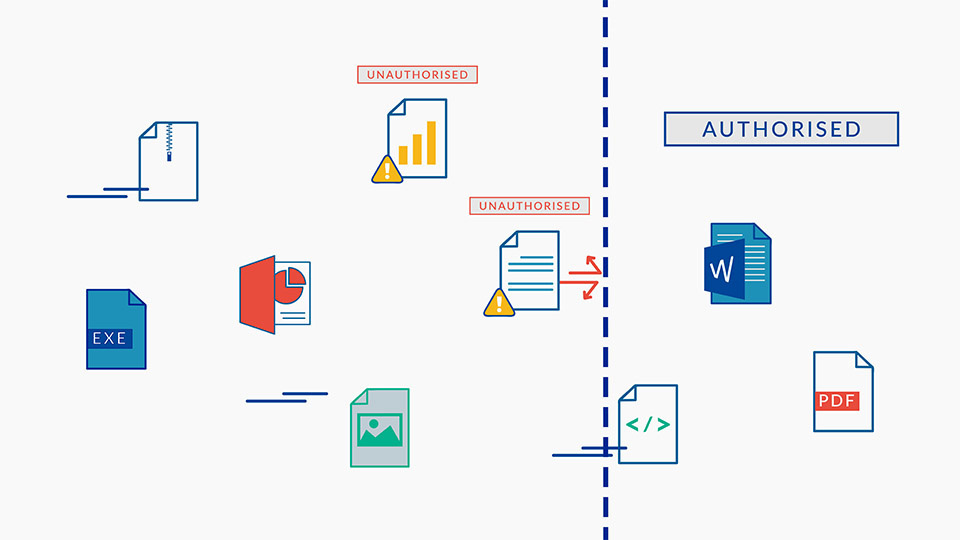
- Administrative oversight over control of trusted applications
- Allows customized configurations for granular policy settings
- Cloud storageto safely access your Data anywhere, anytime and from any device
- Non-reliance on cloud vendors for the protection of your Data
- Persistent and pervasive protection of files moved to GSuite, Office365, Dropbox, OneDrive
- Create and mount virtual disks on all Windows platforms
- Simply drag and drop to encrypt and decrypt shared files
- Authenticate and control with digital signing for added security
- Flexibly manage multiple volumes at preferred sizes
- Securely sign documents so recipients can be assured they are from the original sender
- Permanently delete documents without leaving a trace
- Built-in key and signature management
This is a comprehensive PKI-based feature that secures ALL files with 256-bit AES (Advanced Encryption Standard) file encryption, digital signing and digital rights management (DRM). ALL files are protected from unwanted tampering and interception ensuring privacy, integrity, and authenticity.

- Administrative oversight over control of trusted applications
- Allows customized configurations for granular policy settings

- Non-reliance on cloud vendors for the protection of your Data
- Persistent and pervasive protection of files moved to GSuite, Office365, Dropbox, OneDrive
Achieve inherent compliance for today and tomorrow

ISO 27001
Our ISO certification proves that we meet the highest standards for establishing, implementing, maintaining, and continually improving information security management systems (ISMS).

Common Criteria Certification
Our SecureData encryption technology is currently under evaluation for certification to meet strict security requirements for National Security Procurement.

Federal Information Processing Standards (FIPS)
Our SecureData encryption technology is currently under evaluation for certification to further demonstrate our compliance with industry-leading security standards.

EU General Data Protection Regulation (GDPR)
Our Security Suite fulfils compliance standards protecting individual personal data usage under GDPR.

Health Insurance Portability and Accountability Act (HIPAA)
Our Security Suite fulfils compliance standards surrounding patient health information as required by HIPAA.

Payment Card Industry Data Security Standard (PCI-DSS)
Our Security Suite protects the security of personal cardholder data as required by PCI-DSS.
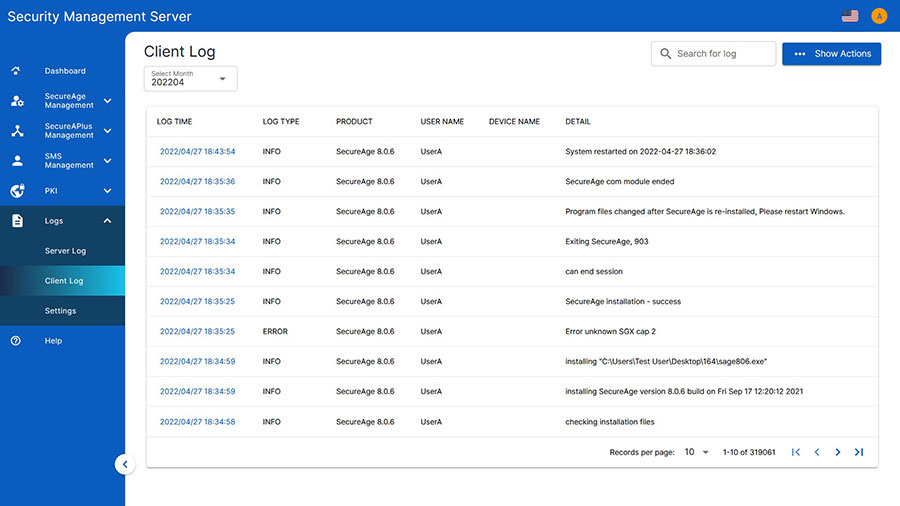
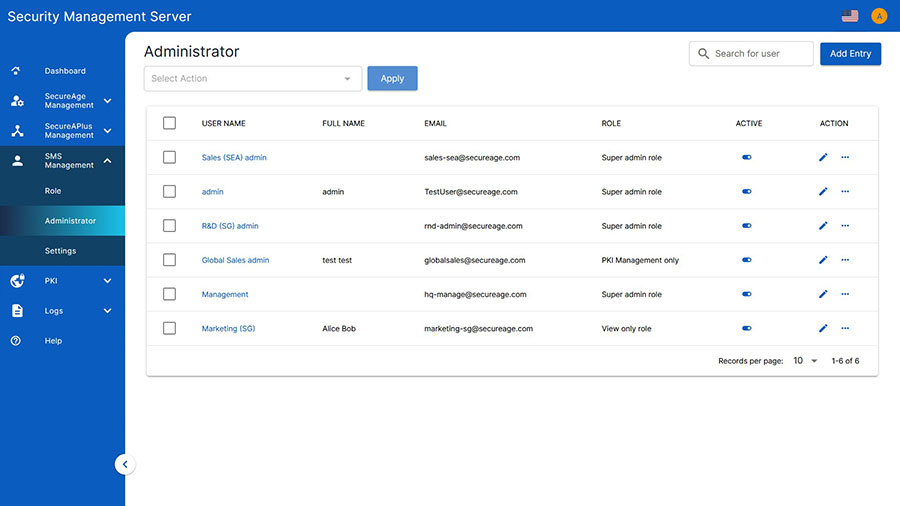
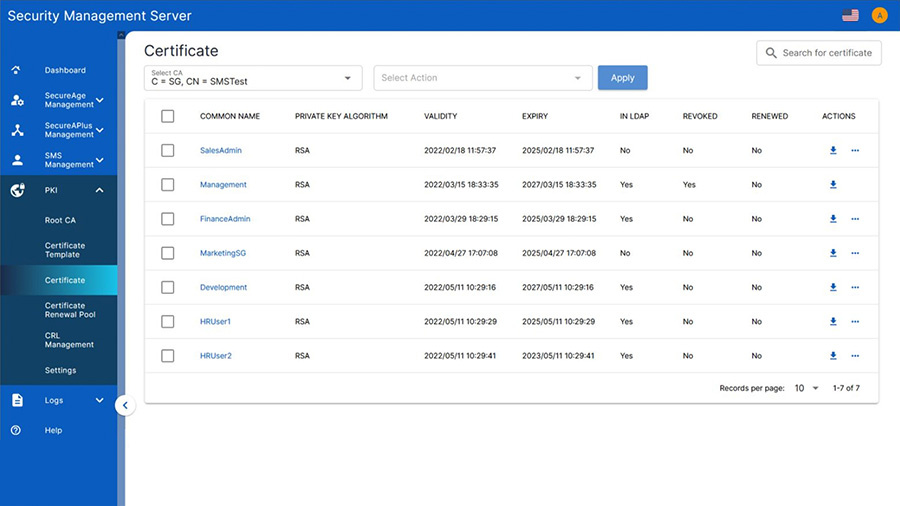
Frequently asked questions about our file encryption software
The SecureAge Security Suite is licensed per-endpoint, with either a subscription-based or perpetual license option.
The basic SecureAge Security Suite includes either SecureData or SecureEmail. The extended SecureAge Security Suite includes SecureData, SecureEmail, SecureDisk, DRM and digital signing, Application control, and Cloud storage.
We offer training, consultancy and maintenance services to ensure a smooth deployment and on-going operations support.
The SecureAge Security Suite works on all Windows platforms and will soon be available on Linux and Mac platforms. Contact us for more information on the status of Linux and Mac compatibility.
With the SecureAge Security Suite there is no access to any file without the SecureAge agent. The pervasive encryption and application binding prevents the product from being disabled by a malicious actor. In addition, our AI-powered endpoint protection solution (CatchPulse) is linked to our PKI-based encryption functionality. That means if it is ever disabled, no files would be accessible.
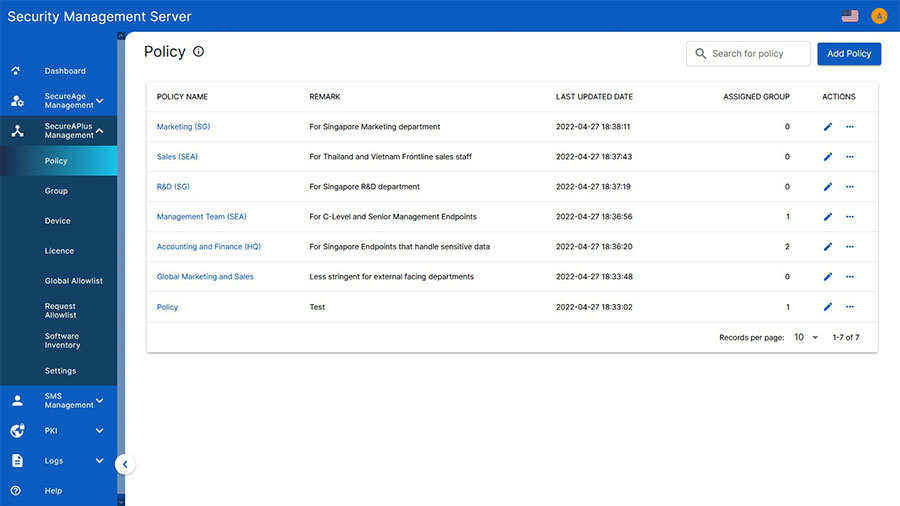
For further security, online and offline policy controls can be added for different individuals or groups of users. “Online” means that the end-user is connected to the Security Management Server (within the network) and “Offline” means that they’re not. With detailed logging functionality, the Security Management Server collects logs from itself and from all endpoints. If the Security Management Server is unavailable for a defined period of time (e.g. when the user is offline) logs are maintained by the client for 2 days by default.
Email encryption features are available through Microsoft Office 365 if users have E3 subscriptions and above and can configure their settings through Azure Information Protection. When signed in, recipients can receive encrypted messages with Office 365 Message Encryption (OME) which decrypts in the Microsoft server with the recipient’s private key that is stored there. OME also has the option to generate a one-time password requiring recipients to validate their identity before accessing.
Read how our technology avoids the gaps in server based processing and authenticates each file for each user at the endpoint.
SecureEmail allows users to exchange encrypted emails with other people outside of the organisation (i.e. those that do not have the SecureAge Security Suite). When using this feature the entire email body and any attachment will be encrypted to ensure 100% privacy. Recipients will be prompted to verify their email address in order to obtain the password to decrypt.
SecureEmail works with S/MIME which is a widely accepted e-mail protocol that is supported by most commonly used email providers such as outlook and apple mail. S/MIME is an important Simple Mail Transfer Protocol (SMTP) which allows for widespread and secure email connectivity.
The most popular PGP model is the open PGP model. The open PGP model follows a decentralized ‘web-of-trust’ model whereby each user decides whether or not they trust another user – there is no central authority or standards which manage identity verification, or which govern the level of trust. Users determine their own standards for identity verification, meaning that each person needs to make the security decision whether to trust someone else's digital identity. To use open PGP, users will have to download, install and complete the set-up themselves in their email program. SecureAge Security Suite email does everything for the end-user behind the scenes, removing the human element from Data security concerns.
Application Binding can be used to create a Data sandbox which prevents advanced persistent threats. It combats these threats by allowing you to set your own special rules as to which circumstances a file should be decrypted / encrypted thereby ensuring files are only opened by certain applications (eg: only Microsoft Word can open .doc files). This prevents reading / editing of files from any other application such as Adobe Reader).
This is useful for high risk applications such as web browsers. For instance, if Internet Explorer is attacked or compromised, only those path directories accessible to Internet Explorer will be affected, all other user systems and Data remain intact.
The SecureAge Security Suite is designed to support any form of multi-factor authentication. This includes seamless integration with passwords and key cards or USB tokens. It is interoperable with all PKCS#11 based secure devices including Smart Cards, Security Tokens, or Hardware Security Modules (HSM).
1. Log files and backup files. A recent Data theft of an online service simply involved the attacker gaining access to log files which contained personally identifiable customer information. With SecureData these logs would have been encrypted. While most backup software includes encryption capabilities, the systems administrator will be able to access any Data within the backup. Microsoft AIP encrypts specific files copied to the backup but all other files will remain unprotected in the backup.
2. Temporary files and the system swap file. Many applications create temporary files that often exist purely for the duration of the application's execution. Microsoft AIP recommends BitLocker for temporary file protection even though it does not work for a live system. With SecureData, live temporary files are protected. As applications execute, portions of their memory space may be held in the swap file. With SecureData this information is encrypted and useless to hackers.
3. Files from legacy applications. Since SecureData operates at the file level, applications do not require knowledge of how to decrypt or encrypt files or how to authorise or deny Data access. Microsoft AIP supports limited versions of Windows and Windows Server.
4. ALL database files. Organisations operate multiple databases, often using different database versions and even different vendors. With SecureData, all database files, structured or unstructured, no matter the version or vendor are encrypted and managed centrally. Microsoft TDE (Transparent Database Encryption) only supports files from specific versions of Microsoft applications and requires a different product for each vendor and versions of their databases.
For enterprises that use SharePoint Server for collaboration among team members, our SecureData technology automatically protects all files that are dragged and dropped into the SharePoint server. This means, only authorised collaborators with the right key are able to access, read, and edit the information contained within SharePoint. This limits involvement by the users and it protects unauthorised insiders or unwanted external sniffers from stealing any information.
Further mitigating the risk of Data leakage is the Data access audit logs which capture details about every file accessed on SharePoint including movement of files out of SharePoint. This Data log helps administrators identify the cause of any anomalies.