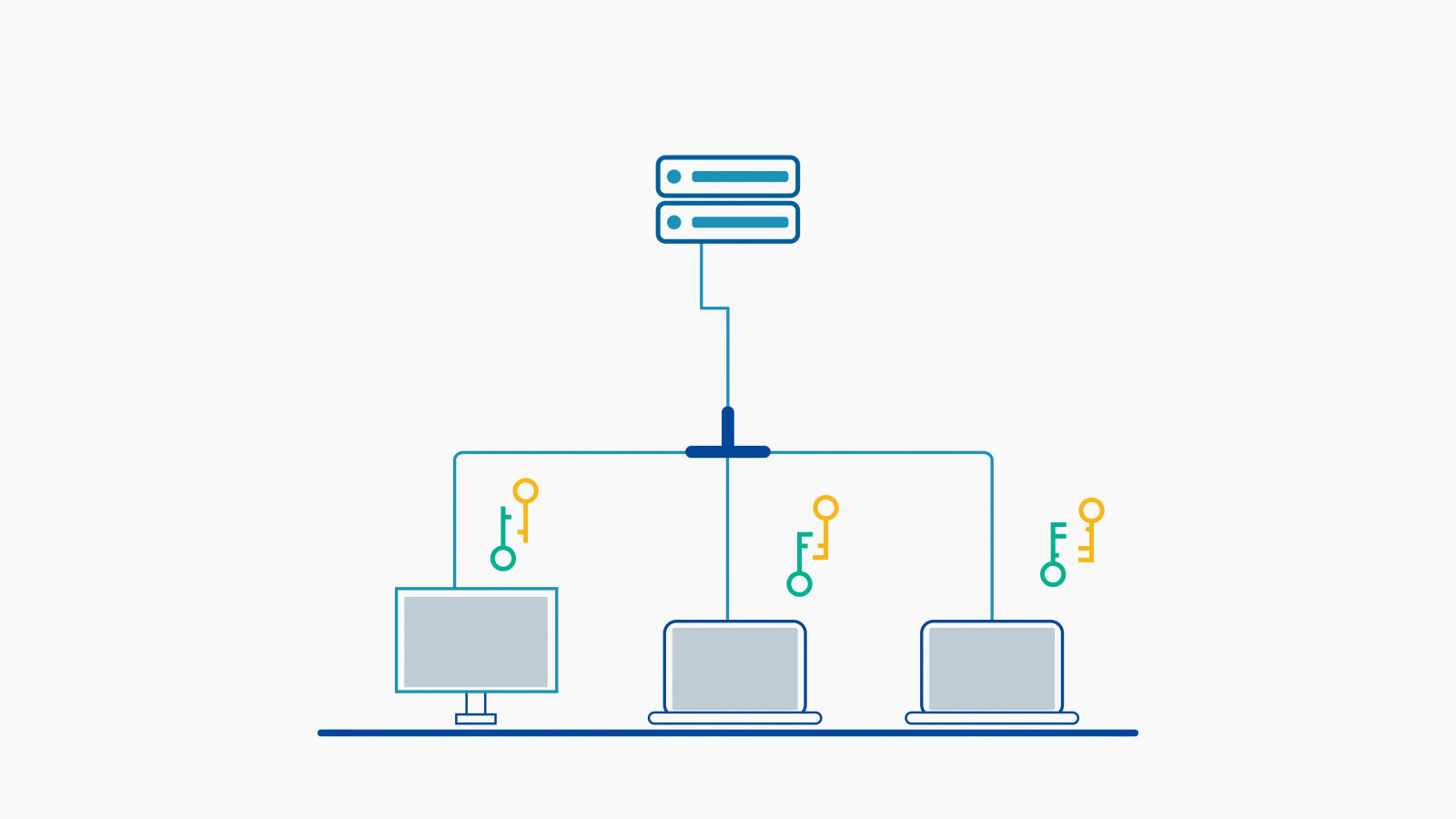
Every file, every place, every time
While there are endless File and Folder Encryption (FFE) products on the market, not all are created equal. Many File Level Encryption (FLE) solutions establish security silos for “sensitive” Data or Data users deem the most important, and even then not in all three states (in-transit, in-use, and at-rest). The problem is, in today’s highly connected and work everywhere world, isn’t all Data important?
With our unique approach to Data encryption, you no longer have to decide what Data to protect. Our SecureData technology protects everything, in every place, all the time. It does this by making encryption an inherent property of your Data, as opposed to a collection of reactive systems, restrictive tools that impact usability, and incomplete policies that can never keep up.
How to choose the best encryption software
Does the encryption software offer proactive protection?
If there’s anything the past few years have taught us, it’s that all the bells, whistles, and consulting in the world can’t predict the future. To stay ahead of every threat, every time, proactiveness is key. The problem is, many encryption solutions require active user involvement. If the approach isn’t completely proactive and it places a burden on the user, it’s only natural that these users will find their own (unsecure) methods to get on with their day-to-day work.
Our approach removes the human element to make protection an inherent part of the Data.
Is the encryption software designed to provide 100% protection?
Full Disk Encryption (FDE or sometimes volume encryption) that protects nominated storage devices sounds powerful but the reality is, it only protects Data on a dormant system (please see the FAQs below on the distinction between FDE and File Level Encryption or FLE). To us, security is either 100% or 0% and our FLE is really 100% for every file, every place, and every time.
Our encryption software can be configured to provide this 100% protection. We protect every file (including those on legacy and in-house custom applications), every place (from endpoints to the cloud and back), and every time (in-transit, in-use, and at-rest).
Is the encryption software protecting Data at the endpoints?
It’s important to ensure that the Data protection is provided at the point where it’s being processed so that there are no security gaps, and that no Data in any state (in-transit, in-use, and at-rest) is left vulnerable. When encryption is processed at a server instead of at the endpoint, it leaves gaps that can result in Data being unavailable for legitimate users, available to unauthorized users, or even sent across networks unprotected.
Our approach protects each and every file at the endpoint and everywhere else.
Other frequently asked questions about Data encryption
File Level Encryption (FLE), on the other hand, encrypts individuals files with or without actions by the end-user. This encryption can remain whether the computer is on or off, whether the file is open or closed, and whether those files are moving or are at-rest. The SecureAge approach to FLE includes the benefits of FDE for Data files at-rest and also extends protection to files in-transit and in-use; every file, every place, and every time.
In other words, the “full” in FDE does not mean what most people think it does – real Data security provides protection for 100% of your files in all three states of usage, anywhere they go, and any way they’re used.
Our PKI-based encryption is faster than the graphical user interface which makes it so fast that your employees will never notice. We "stream" Data from the disk, through our encryption engine and into memory so the application does not need to wait for the whole file to be decrypted before use. In fact, the file remains encrypted on disk all of the time.
Modern processors will provide an instruction set specifically for encryption so these security activities do not rob any time from your normal processing cycles. Our government clients who run large databases and typically experience performance hits (due to the combination of CPU, RAM, hard drive performance, and network connection), have been able to minimise performance impact with our solutions.
SecureData seamlessly supports Databases. Many organisations have to maintain database systems from different vendors, and purchasing the vendor-specific TDE (Transparent Data Encryption) add-on for each database is expensive. SecureData supports every database system without causing any disruption and requiring no additional database configuration. And because SecureData encrypts all files, you can be assured that sensitive Data held in report, log and temporary files, in addition to unstructured Data, will remain encrypted all the time.
Databases can of course be very large, but SecureData still keeps Data held in the file system encrypted all the time. As each "page" of Data is passed into system memory it is decrypted - not the whole database. This approach ensures good performance while keeping stored Data secure. From the user's point of view there is no difference - they can still work in exactly the same way, running reports, searches and other transactions.
Our unique approach also allows us to plug in any encryption algorithm that our customers prefer. Many of our government and research clients prefer their own bespoke algorithms and we’re able to extend that level of comfort and compliance to everyone, everywhere.
SecureAge uses PKI-based asymmetric encryption to remove the trade-off between proven Data Security and Usability. End users don’t even need to be aware that they are using SecureAge and can work as they normally do, sharing files securely and thinking about things other than cybersecurity.
SecureAge encryption is compatible with DLP tools and procedures, allowing all processes to run on the same machine without interruption (e.g. content searches, database queries, other scanning). Every approved application on a system can access all of the encrypted data in real time as if the Data is not encrypted at all. Unlike competitive encryption techniques, SecureAge technology seamlessly integrates with your favourite DLP solutions and more.
But when that machine is turned on, the encryption key is entered, and the hard disk is spinning so that the Data on it can be used, FDE no longer protects any of it. All of the files can be removed as plain, unencrypted Data.
FDE is great if someone steals your laptop from your bag. But it's not so great for the way real people use and lose Data every day. We need to turn our machines on to access our Data, and that’s precisely when FDE can’t help.
TDE does not protect the vendor’s temporary and log files. TDE considers temporary, log and report files unimportant and as a result, they are unsecured. These files can, however, can contain sensitive or proprietary information.
TDE is database-specific, meaning you'll need separate TDE licences for each database software, and each license will need to be managed separately - costly and time consuming.
Homomorphic encryption requires application modifications. Businesses will need to rewrite or modify their original or more free-form applications whereas our PKI-based encryption does not interfere with other applications and works alongside them.
FPE is limited to one algorithm, the Advanced Encryption Standard (AES) which NIST identified as “no longer suitable as a general purpose FPE method. While AES can be part of your solution, it can’t be your entire solution.
Hyper FPE sounds even cooler but it requires significant trade-offs between Data protection and usability; our belief is that only inherent and invisible protection without user involvement is truly secure 100% of the time. Hyper FPE also requires that some Data be plain to run certain type of analytics and applications.
Tokenization negatively impacts performance because it can’t take advantage of the AES-NI subset of Intel processors like encryption can, directly hitting the CPU.
Our technology has a 19-year history of ZERO plain Data breaches
This proactive and pervasive style of Data protection quickly attracted governments who were trying to overcome the problems caused by reactive systems, restrictive tools, and constantly changing cybersecurity policies. SecureData has been the encryption solution of choice for public entities in Singapore, Tokyo, and Hong Kong since 2003.
Industry certified

Our internal Data security and information management systems received ISO 27001 certification from SOCOTEC Certification International in 2013.
This ongoing certification ensures that our headquarters remains compliant with ISO 27001 information security management standards for all on-premise Data held.

Our unique encryption technology, SecureData is undergoing Common Criteria Certification to certify the reliability, quality and trustworthiness of this solution.
Common Criteria (CC) Certification provides an independent and objective validation and can be relied upon to help make informed IT purchasing decisions. It is recognised across 31 countries, and a requirement of hardware and software devices used for national security by the U.S Federal Government, among others, as well as some highly regulated industries globally.

Regarded as the de-facto standard for encryption by both government and non-government organisations, FIPS certification is considered the minimum benchmark for cybersecurity standards outside the United States. FIPS Certification has also been adopted by authorities in other countries, including Canada and Japan, as well as across other industries that require high-performing security including the financial, energy, and telecommunications sectors.
We are pleased to inform you that UL Verification Services Inc. (UL) has completed their testing of SecureData and submitted a Validation Test Report to the Cryptographic Model Validation Program (CMVP) recommending they issue a certificate of validation.